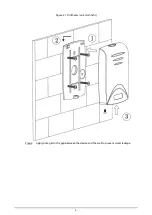
Reviews:
No comments
Related manuals for DHI-ASR1100B

RMD 032
Brand: Caliber Pages: 4

RDD 571BT
Brand: Caliber Pages: 34

MS926P
Brand: Unitech Pages: 2

MS912+
Brand: Unitech Pages: 17

MS912
Brand: Unitech Pages: 6

MS842
Brand: Unitech Pages: 2

MS840P
Brand: Unitech Pages: 2

HT630
Brand: Unitech Pages: 3

404
Brand: E-Mu Pages: 12

QuickScan QM2430-BK-433K2
Brand: Datalogic Pages: 40

BHT-300B
Brand: Denso Pages: 178

AVN76D
Brand: Eclipse Pages: 215

FuzzyScan FA460
Brand: Cino Pages: 67

QuickScan QBT24 series
Brand: Datalogic Pages: 314

CD 2604 MP3 -
Brand: VDO Pages: 26

3131
Brand: H&S Pages: 32

XTA-2000
Brand: Delco Pages: 18

Gigabit Ethernet-SX PCI-X Adapter and Dual...
Brand: IBM Pages: 32