Summary of Contents for Firebox X1000
Page 1: ...WatchGuard Firebox System Reference Guide WatchGuard Firebox System...
Page 12: ...xii WatchGuard Firebox System...
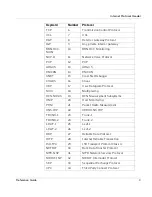
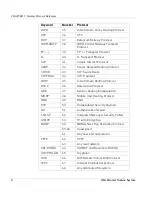
Page 22: ...CHAPTER 1 Internet Protocol Reference 10 WatchGuard Firebox System...
Page 38: ...CHAPTER 2 MIME Content Types 26 WatchGuard Firebox System...
Page 92: ...CHAPTER 5 Common Log Messages 80 WatchGuard Firebox System...
Page 118: ...CHAPTER 8 Firebox Read Only System Area 106 WatchGuard Firebox System...
Page 164: ...CHAPTER 9 Glossary 152 WatchGuard Firebox System...