52
•
Configuration
HP NonStop SSL Reference Manual
Example
CONTENTFILTER CFILTER
Considerations
•
The value of the parameter can be changed without stopping HP NonStop SSL using the SSLCOM command
SET CONTENTFILTER file.
•
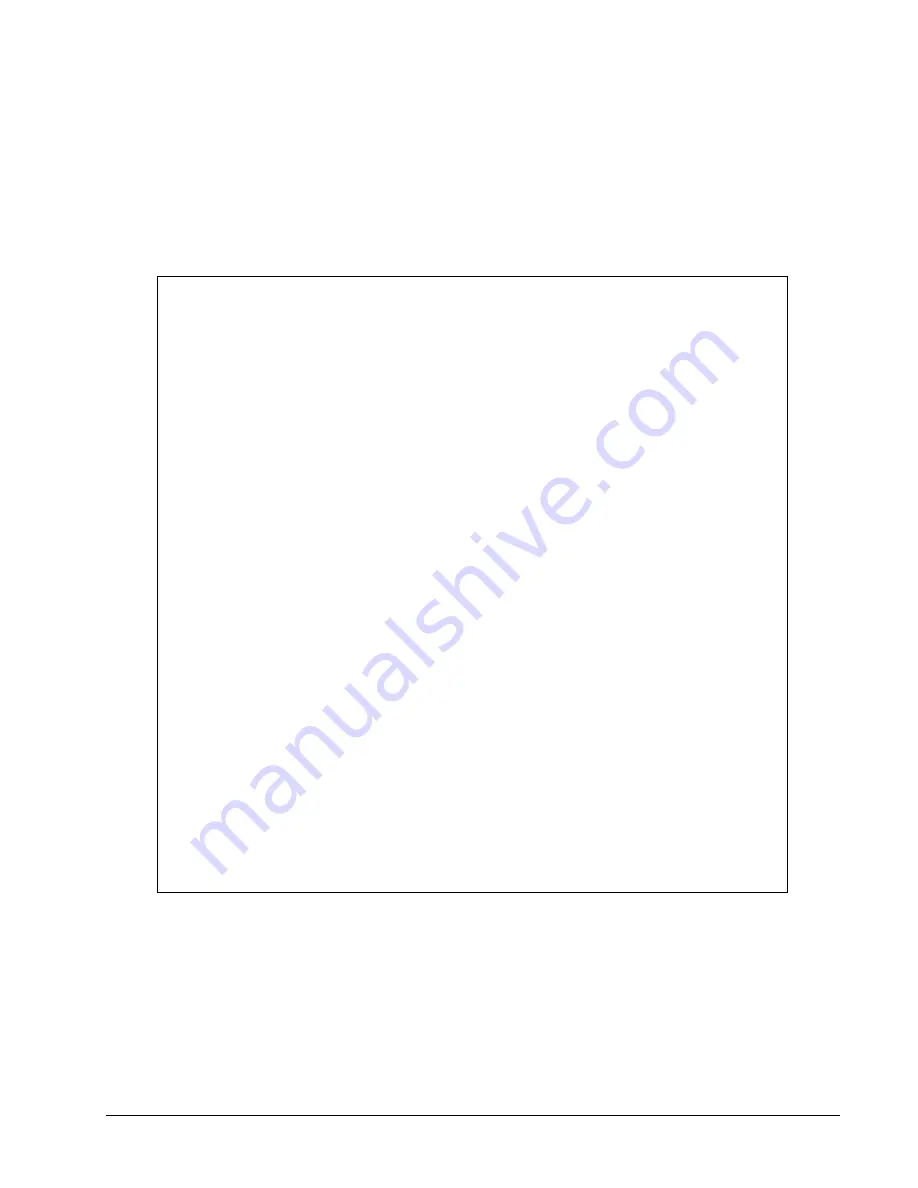
The following example shows the syntax of the filter rules. This example will only allow messages starting with
"<A" or "<B" and ending with ">" to pass the filter.
#################################################################################
# file to define content filter rules
# empty lines or lines starting with '#' are ignored
#################################################################################
#################################################################################
# example file based on the following requirements:
#
# the following two are valid messages (double quotes are *not* part of msg)
# "<ABC>"
# "<BBC>"
#
# the following two are *not* valid messages
# "<CCC>" - does not start with "<A" or "<B"
# "text" - does not start with "<"
#################################################################################
#################################################################################
# msg delimiters (required)
# used to define a "message" as part of the byte stream
# all bytes are ASCII values represented as decimal numbers
#################################################################################
# start with < sign = 3C hex = 60 dec
msgstartbyte 60
# end with > sign = 3E hex = 62 dec
msgendbyte 62
#################################################################################
# list of regular expressions, in double quotes
# (at least one required)
#
# note that the engine implements "traditional unix regular expressions"
# see
# en.wikipedia.org/wiki/Regular_expression#Traditional_Unix_regular_expressions
# for details
#
# regular expressions are combined using an implicit "logical or"
# a message matching any single regular expression will pass
# a message matching no regular expression will fail
# at least one regular expression must be present
#################################################################################
# allow any message starting with "<A"
regexp "^<A."
# allow any message starting with "<B"
regexp "^<B."
Summary of Contents for NonStop SSL
Page 8: ...8 Preface HP NonStop SSL Reference Manual This is the initial version of this manual ...
Page 30: ...30 Installation HP NonStop SSL Reference Manual ...
Page 90: ...90 Monitoring HP NonStop SSL Reference Manual ...
Page 98: ...98 SSLCOM Command Interface HP NonStop SSL Reference Manual ...
Page 110: ...110 SSL Reference HP NonStop SSL Reference Manual ...
Page 116: ...116 Remote SSL Proxy HP NonStop SSL Reference Manual ...