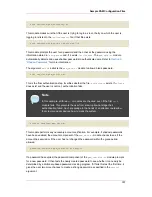
auth required pam_securetty.so
This module makes sure that if the user is trying to log in as root, the tty on which the user is
logging in is listed in the
/etc/securetty
file, if that file exists.
auth required pam_unix.so shadow nullok
This module prompts the user for a password and then checks the password using the
information stored in
/etc/passwd
and, if it exists,
/etc/shadow
. The
pam_unix.so
module
automatically detects and uses shadow passwords to authenticate users. Refer to
Section 5,
“Shadow Passwords”
for more information.
The argument
nullok
instructs the
pam_unix.so
module to allow a blank password.
auth required pam_nologin.so
This is the final authentication step. It verifies whether the file
/etc/nologin
exists. If
nologin
does exist and the user is not root, authentication fails.
Note
In this example, all three
auth
modules are checked, even if the first
auth
module fails. This prevents the user from knowing at what stage their
authentication failed. Such knowledge in the hands of an attacker could allow
them to more easily deduce how to crack the system.
account required pam_unix.so
This module performs any necessary account verification. For example, if shadow passwords
have been enabled, the account component of the
pam_unix.so
module checks to see if the
account has expired or if the user has not changed the password within the grace period
allowed.
password required pam_cracklib.so retry=3
If a password has expired, the password component of the
pam_cracklib.so
module prompts
for a new password. It then tests the newly created password to see whether it can easily be
determined by a dictionary-based password cracking program. If it fails this test the first time, it
gives the user two more chances to create a strong password, as specified in the
retry=3
argument.
Sample PAM Configuration Files
301
Summary of Contents for ENTERPRISE LINUX 4.5.0 -
Page 1: ...Red Hat Enterprise Linux 4 5 0 4 5 0 Reference Guide ISBN N A Publication date ...
Page 2: ...Red Hat Enterprise Linux 4 5 0 ...
Page 4: ...Red Hat Enterprise Linux 4 5 0 ...
Page 24: ...xxiv ...
Page 26: ......
Page 36: ...12 ...
Page 72: ...48 ...
Page 112: ...88 ...
Page 122: ...98 ...
Page 140: ...116 ...
Page 142: ......
Page 300: ...276 ...
Page 318: ...294 ...
Page 320: ......
Page 332: ...308 ...
Page 350: ...326 ...
Page 378: ...354 ...
Page 388: ...364 ...
Page 394: ...370 ...
Page 395: ...Part IV Appendixes ...
Page 396: ......