Introduction
224
SWRU455A – February 2017 – Revised March 2017
Copyright © 2017, Texas Instruments Incorporated
Crypto Utilities
16.1 Introduction
The SimpleLink device supports on-chip asymmetric key-pair storage (secure key storage) with built-in
crypto acceleration and crypto services to assist in some common cryptographic-related operations.
These crypto services provide a mechanism to manage up to eight ECC key-pairs, and use them to sign
or verify data buffers. This capability could be used for authenticating the device identity, among other
usage options.
There are three types of supported key-pairs:
•
Device-unique key-pair: A single 256-bit unique key of the device, embedded in hardware
•
Temporary key-pair: Created upon request using the internal TRNG engine
•
Installed key-pair: Installed and maintained by the vendor
The system supports a single constant key-pair. Entry 0 is reserved for this key-pair. Entries 1 to 7 could
be used for temporary or installed key-pairs, according to the application needs. All keys are ECC keys
using the SECP256R1 curve. This applies to all entries:
•
Constant and temporary key types – The SimpleLink Wi-Fi device is responsible for using the correct
type and curve.
•
Installed key type – The vendor is responsible only for installing keys of this type and curves.
For all key pairs, the private key is never exposed, and can only be accessed indirectly when using it to
sign buffers. The public key may be retrieved by the host application (see
lists
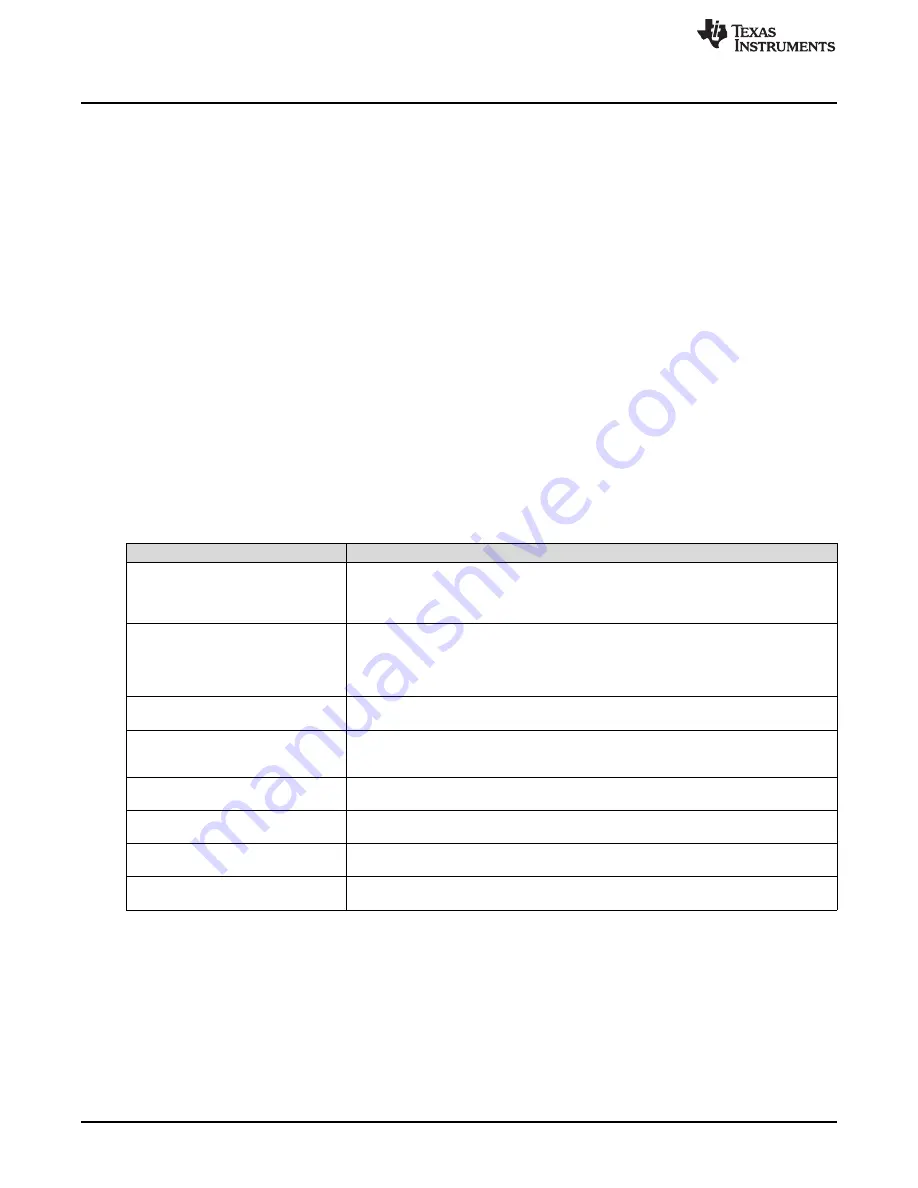
the key crypto utility features.
Table 16-1. Key Features
Main Features
Description
Manage temporary key-pair
Create or remove temporary keys at a provided index. Temporary keys are not persistent
over the power cycle. Creating a temporary key in an index occupied by another
temporary key, and overrides the occupied key. An installed key on that index cannot be
overridden.
Installed key-pairs
Install or uninstall key pairs provided by the host application. The keys must be
preprogrammed in the file system. The install action adds them to the data base, and
allows using them to sign and verify buffers. This operation is persistent over the power
cycle without consideration of system-persistent configuration. Cannot install a key in an
occupied index.
Constant key-pair
Unique key for the given device, embedded in the hardware. Always available and
constant.
Retrieve public key
For any key-pair type, the host may request to retrieve the public key of the pair in x9.63
raw format. The host application can also retrieve the metadata of this key (type, curve,
length, filename, and so forth).
Verify buffer
Given a buffer and a signature, the host can request to use any key-pair to verify the
ECDSA signature.
Sign buffer
Given a buffer, the host can request to use any key-pair to create a signature using
ECDSA.
Secured content delivery
Transfer secure content by sending the public key to the application server which
encrypts the file, and decrypts in the device internally using the private key only
True random number
Retrieve buffer with true random numbers from the networking subsystem. Maximum
buffer length 172 bytes for each retrieval.
16.1.1 API and Usage
16.1.1.1 Install and Uninstall Key-Pairs
This command is used to install and uninstall a key-pair in one of the crypto utilities key-pair management
mechanism. The key must be an ECC key-pair using the SECP256R1 curve, and already programmed to
the file system in a DER format file. The install and uninstall operations are done using the sl_NetUtilsCmd
API. The key installation is persistent without consideration of system-persistent configuration, and is not
erased over the power cycle. If the wanted index is already occupied by a key-pair, the install operation
fails.