6.7.1 PIN code
Protected data access is only possible after unlocking the configuration memory with the correct 32 bit PIN
code. By default, the protected area is locked and the default pin code for unlocking access is 0x0000E215.
The default pin code shall be changed to a user-defined value as part of the installation process. This can be
done by unlocking the NFC interface with the old PIN code and then writing the new PIN code to page 0xE5 as
described in chapter 6.3.1.
6.7.2 Configuration of product parameters
SR-SBP2801-BLE-E allows no direct modification of the following parameters:
1.Static Source Address
2.Product ID
3.Manufacturer ID
4.Security Key
In order to modify these parameters, the user has to write the new value into specific registers (Source Address
Write, Product ID Write, Manufacturer ID Write and Security Key Write) in the protected data area and set the
according Update flag in the Configuration register.
After that, the user has to push and release the button of the SR-SBP2801-BLE-E module.
6.7.3 Configuration register
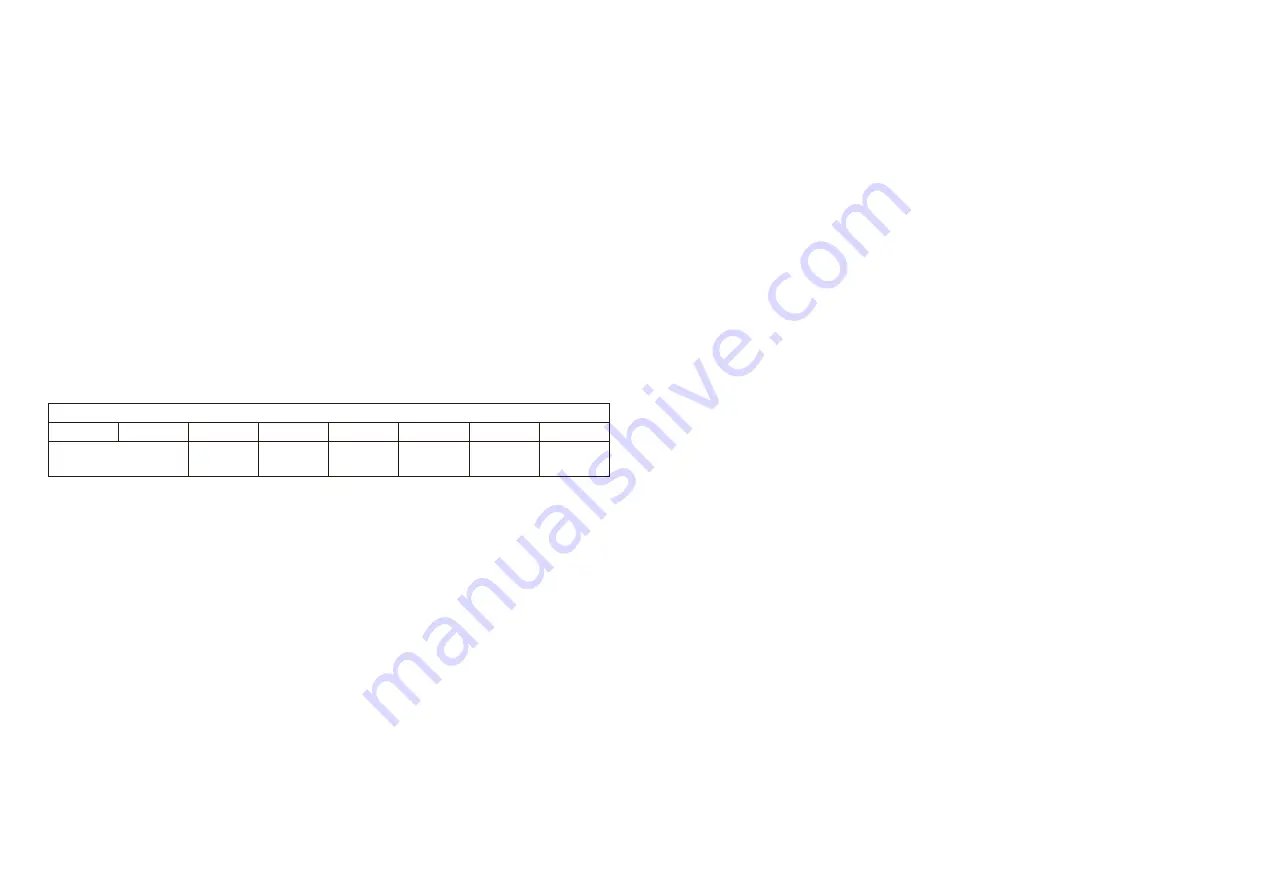
The Configuration register is 1 byte wide and contains configuration flags. Figure 30 below shows the structure
of the Configuration register.
CONFIGURATION
Bit 7
Bit 6
Bit 5
Bit 4
Bit 3
Bit 2
Bit 1
Bit 0
OPTIONAL D ATA S IZE
DISAB LE LR N
TELEGRAM
RPA ADDRESS
MODE
PRIVATE
SECUR ITY KEY
UPD ATE
SECUR ITY KEY
UPD ATE
MAN ID
UPD ATE
SOURCE ID
Figure 30 – Configuration register structure
The Configuration register is used to select the length of optional data, to disable the transmission of
commissioning telegrams, to select resolvable private address mode, to disable NFC read-out of the security
key and to indicate an update of the security key, the manufacturer ID or the source ID.
6.7.4 Source Address Write register
The Source Address Write register is 4 byte wide and can be used to modify the lower 32 bit of the SR-
SBP2801-BLE-E Static Source Address. The upper 16 bit of the SR-SBP2801-BLE-E Static Source Address
are always fixed to 0xE215 to identify the device type. In order to do change the lower 32 bit of the Static
Source Address, follow these steps:
1. Write new source address into the Source Address Write register
2. Set the UPDATE SOURCE ID flag in the Configuration register to 0b1
3. Actuate (press and release) the button of SR-SBP2801-BLE-E
SR-SBP2801-BLE-E will determine that it should modify the Static Source Address based on the set- ting of the
Update Source ID flag and copy the value of the Source Address Write register
to the lower 32 bit of the Source Address register. After successful execution, SR-SBP2801-BLE-E will clear
the UPDATE SOURCE ID flag to 0b0.
6.7.5 Security Key Write register
The Security Key Write register is 16 byte wide and contains the device-unique random security key. The
factory programmed key can be replaced with a user defined key by fol- lowing these steps:
1. Write new security key into the Security Key Write register
Note that for security reasons, setting the Security Key to the following values is not possible:
•0x00000000000000000000000000000000
•0xFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
If the Security Key Write register is set to one of these values then no update of the Security Key will occur.
2. Set the UPDATE SECURITY KEY flag in the Configuration register to 0b1
3. If the key should be write-only (not readable after the key update) then set the Private Security Key flag in
the Configuration register to 0b1
4. Actuate (press and release) the button of SR-SBP2801-BLE-E
SR-SBP2801-BLE-E will determine that it should modify the security key based on the setting of the Update
Security Key flag and copy the value of the Security Key Write register to the Security Key register in private
memory. After successful execution, SR-SBP2801-BLE-E will clear the UPDATE SECURITY KEY flag to 0b0.
The protected memory is designed to support 1000 modifications of the security key.
Note that it is not possible to read the current security key via NFC if the Security Key Write register has been
accidentally overwritten or cleared via NFC write. In this case it is necessary to write a new security key (as
described above) or to reset the device to its de- fault security key by means of a factory reset.
6.7.6 Private Security Key mode
SR-SBP2801-BLE-E provides a private security key mode for applications requiring high security. In this mode,
it is possible to write a security key which subsequently is inaccessible via NFC and will not show up in
commissioning telegram. In both cases, the security key will be set to all zeros. The written security key thereby
is completely inaccessible externally.
To use private security key mode, set the PRIVATE SECURITY KEY flag in the Configuration register is to 0b1,
the Security Key Write register to the desired security key and the UP- DATE SECURITY KEY flag in the
Configuration register is to 0b1 and pushing the button.
The Security Key Write register will be cleared to 0x00000000000000000000000000000000 after successful
execution and the written security key will not be NFC readable (even for users having the correct PIN code). If
commissioning telegrams are enabled then the secu- rity key will be set to
0x00000000000000000000000000000000 there as well.
It is possible to return to Public (NFC-accessible) key mode by clearing the PRIVATE SECURI- TY KEY flag in
the Configuration register, setting the Security Key Write register to the desired security key and the UPDATE
SECURITY KEY flag in the Configuration register is to
0b1 and pushing the button.
The protected memory is designed to support 1000 modifications of the security key.
6.7.7 Product ID and Manufacturer ID Write register
The Product ID register is 8 byte wide and can be used to specify a publicly-accessible parameter (e.g. a user-
specific ID or name) that can be read by an NFC commissioning tool in order to determine the specific product
type.
The Manufacturer ID is 2 byte wide and specifies the manufacturer of a BLE product and is transmitted as part
of each BLE telegram. By default, the manufacturer ID is set to 0x0A78 (Sunricher) but it can be changed to a
different OEM identifier.
Product ID and Manufacturer ID can be changed by following these steps:
1. Write the desired Product ID (8 byte using HEX or ASCII encoding according to user choice) into the Product
ID Write register. Setting the Product ID register to
0x0000000000000000 will cause SR-SBP2801-BLE-E not to update the Product ID.
2. Write the desired Manufacturer ID (2 byte) into the Manufacturer ID Write register.
Setting the Manufacturer ID Write register to 0x0000 will cause SR-SBP2801-BLE-E not to update the
Manufacturer ID.
3. Set the UPDATE MAN ID flag in the Configuration register to 0b1
4. Actuate (press and release) the button of SR-SBP2801-BLE-E
SR-SBP2801-BLE-E will determine that it should update the Product ID and Manufacturer ID based on the
setting of the Update Product and Manufacturer ID flag and copy any non-zero value of the Product ID Write
register to the Product ID register and any non-zero value of the Manufacturer ID Write Register to the
Manufacturer ID register.







































