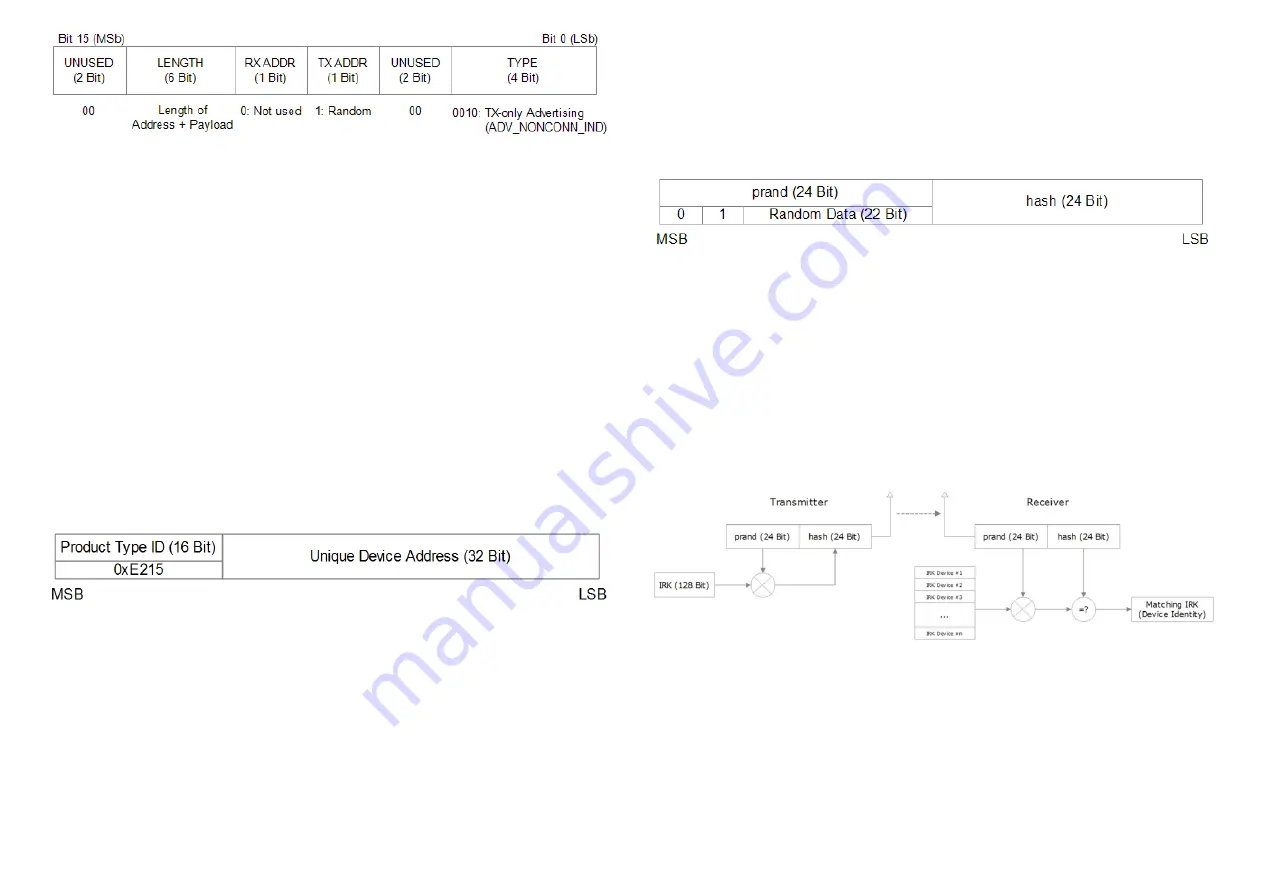
4.4 Source address
The 6 byte BLE Source Address (MAC address) uniquely identifies each SR-SBP2801-BLE-E product. SR-
SBP2801-BLE-E supports two source address modes:
1. Static Source Address mode (default)
In this mode, the source address is constant (but its lower 32 bit can be configured via NFC interface)
2. Resolvable Private Address mode (NFC configurable option)
In this mode, the source address changes for each transmission
By default, SR-SBP2801-BLE-E uses Static Source Address mode. Private Resolvable Address mode can be
selected by setting the Private Source Address flag in the Configuration register (see chapter 6.7.3) to 0b1.
These two address modes are described in the following chapters.
4.4.1 Static source address mode
By default, SR-SBP2801-BLE-E uses static source addresses meaning that the source address is constant
during normal operation. The static source address can be read and configured (written) via NFC as described
in chapter 6.
The structure of SR-SBP2801-BLE-E static addresses is as follows:
1.The upper 2 bytes of the source address are used to identify the device type and set to 0xE215 for all SR-
SBP2801-BLE-E devices (to designate Sunricher SBP 2801 device type). These two bytes cannot be changed.
2.The lower 4 bytes are uniquely assigned to each device. They can be changed using the NFC configuration
interface as described in chapter 6.7.4
Figure 11 below illustrates the static address structure used by SR-SBP2801-BLE-E.
Figure 11 – BLE static source address structure
4.4.2 Resolvable private address mode
For some applications it is desirable to obfuscate the origins of SR-SBP2801-BLE-E data telegrams in order to
prevent tracking of its radio transmissions. This can be achieved by using resolvable private addresses (RPA)
as defined in the Bluetooth Core Specification.
SR-SBP2801-BLE-E can be configured to use resolvable private addresses by setting the RPA ADDRESS
MODE flag within the Configuration register (described in chapter 6.7.3) to 0b1.
When using resolvable private addresses, the address used by SR-SBP2801-BLE-E is modified (rotated)
according to a defined scheme which on one hand precludes determining the device identity by unauthorized
receivers while allowing authorized receivers (sharing a specific security key with SR-SBP2801-BLE-E) to do
so.
The shared security key – which has to be known by both SR-SBP2801-BLE-E and the authorized receiver – is
called the Identity Resolution Key (IRK). SR-SBP2801-BLE-E uses its device-unique random key as identity
resolution key. This key can be modified if needed via the NFC configuration interface as described in chapter
6.7.5.
For each data telegram transmitted by SR-SBP2801-BLE-E (i.e. for every button push or release), a new
Figure 12 – BLE resolvable private address structure
The prand value is encrypted using the IRK. The lowest 24 bit of the result (encrypted val- ue) are then used as
hash. The concatenation of 24 bit prand and 24 bit hash will be transmitted as 48 bit private resolvable source
address.
The receiver maintains a list of IRK for all transmitters that have been commissioned to work with it.
Whenever the receiver receives a data telegram with a resolvable private address (identified by the most
significant bits of the address field being set to 0b10), it will itself generate a 24 bit hash from the 24 bit prand
sequentially using each IRK known to it (i.e. the IRK of each device that has been learned into it).
If an IRK matches (i.e. when prand is encoded with the IRK then the result matches hash), then the receiver has
established the IRK used by the transmitter and thereby the identity of the transmitter.
So conceptually the IRK takes the role of the device address of the transmitter while prand and hash provide a
mechanism for the receiver to select the correct IRK among the set of IRK known to it.
This mechanism is illustrated in Figure 13 below.
Refer to Appendix B for an example of resolving a resolvable private address.
Note that commissioning telegrams (as described in chapter 5.3.2) always use static source addresses (as
described in chapter 4.4.1) since they establish the device identity and contain the IRK in the payload.
4.5 Check Sum
The 3 byte BLE Check Sum is used to verify data integrity of received BLE radio telegrams. It is calculated as
CRC (cyclic redundancy check) of the BLE Header, Source Address and Payload fields.
4.6 Telegram payload
SR-SBP2801-BLE-E can transmit two types of telegrams:
1.Data telegrams
The payload of data telegrams contains the switch status together with optional data
Figure 13 – Resolving private addresses
Figure 10 – BLE header structure
resolvable private address is generated. The 48 bit address field of such resolvable private address is split into
two sub-fields:
1.prand
This field contains a random number which always starts (two most significant bits) with 0b10. The prand value
is changed for each telegram that is transmitted. Individual advertising events used to transmit one telegram
(as described in chapter 3) use the same prand value.
2.hash
This field contains a verification value (hash) generated from prand using the IRK The structure of a resolvable
private address is shown in Figure 12 below.