© Copyright 2007 Cisco Systems, Inc.
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
23
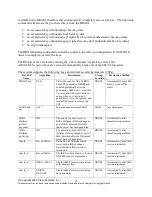
AAA server is zeroized upon
completion of the authentication
attempt.
PPP
authentication
key
RFC 1334
The authentication key used in
PPP. This key is in the DRAM and
not zeroized at runtime. One can
turn off the router to zeroize this
key because it is stored in DRAM.
DRAM
Turn off the router.
Router
authentication
key 2
Shared Secret
This key is used by the router to
authenticate itself to the peer. The
key is identical to Router
authentication key 1 except that it
is retrieved from the local database
(on the router itself). Issuing the
“no username password” zeroizes
the password (that is used as this
key) from the local database.
NVRAM
“# no username
password”
SSH session
key
Various
symmetric
This is the SSH session key. It is
zeroized when the SSH session is
terminated.
DRAM
Automatically when
SSH session terminated
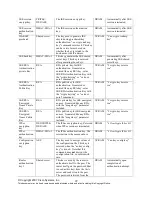
User password Shared Secret
The password of the User role. This
password is zeroized by
overwriting it with a new password.
NVRAM
Overwrite with new
password
Enable
password
Shared Secret
The plaintext password of the CO
role. This password is zeroized by
overwriting it with a new password.
NVRAM
Overwrite with new
password
Enable secret
Shared Secret
The ciphertext password of the CO
role. However, the algorithm used
to encrypt this password is not
FIPS approved. Therefore, this
password is considered plaintext
for FIPS purposes. This password
is zeroized by overwriting it with a
new password.
NVRAM
Overwrite with new
password
RADIUS
secret
Shared Secret
The RADIUS shared secret. This
shared secret is zeroized by
executing the “no radius-server
key” command.
NVRAM
“# no radius-server key”
secret_1_0_0
The fixed key used in Cisco vendor
ID generation. This key is
embedded in the module binary
image and can be deleted by
erasing the Flash.
NVRAM
Deleted by erasing the
Flash.
secret
Shared Secret
The shared secret. This
shared secret is zeroized by
executing the “no tacacs-server
key” command.
NVRAM
“# no tacacs-server key”
TLS server
private key
RSA
1024/1536/2048 bit RSA private
key used for SSLV3.1/TLS.
NVRAM
“# crypto key zeroize
rsa"
TLS server
public key
RSA
1024/1536/2048 bit RSA public
key used for SSLV3.1/TLS.
NVRAM
“# crypto key zeroize
rsa"
TLS pre-
master secret
Shared Secret
Shared Secret created using
asymmetric cryptography from
which new TLS session keys can
be created
DRAM
Automatically when
TLS session is
terminated