| Installation and Upgrades |
16
Important:
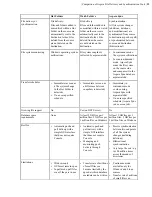
Aspera strongly recommends running the SSH server on a non-default port (allowing inbound SSH
connections on TCP/33001, and disallowing inbound connections on TCP/22) to ensure that your server remains
secure from SSH port scan attacks. For instructions on how to change your SSH port, see
on page 16.
If you have a legacy customer base that uses TCP/22 then you can allow inbound connections on both ports. See
on page 16 for instructions.
The firewall on the server side must allow the open TCP port to reach HST Server. No servers are listening on
UDP ports. When a transfer is initiated by an Aspera client, the client opens an SSH session to the SSH server on
the designated TCP port and negotiates the UDP port for the data transfer.
•
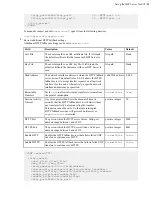
Inbound UDP/33001:
The port for FASP transfers, which use UDP/33001 by default, although the server may
also choose to run FASP transfers on another port.
•
Inbound and outbound TCP/ and TCP 8443 (or other TCP ports set for HTTP/HTTPS fallback):
The ports
for the HTTP fallback. If only HTTP or HTTPS is used, you need to open only that port. For more information on
configuring HTTP fallback ports, see
Configuring HTTP and HTTPS Fallback
on page 29.
•
Inbound TCP/80 and TCP/443:
The ports for the HST Server web UI, for HTTP and/or HTTPS web access. If
only HTTP or HTTPS is used, you only need to open that port.
•
Local firewall:
If you have a local firewall on your server (like
iptables
), verify that it is not blocking your
SSH and FASP transfer ports (such as TCP/UDP 33001). If you are using Vlinks, you will need to allow the Vlink
UDP port (55001, by default) for multicast traffic. For additional information on setting up Vlinks, see
Bandwidth Usage with Virtual Links (Command Line)
on page 58.
Remote Client Machines
Typically, consumer and business firewalls allow direct outbound connections from client computers on TCP and
UDP, and no configuration is required for Aspera transfers. In the special case of firewalls blocking direct outbound
connections, usually with proxy servers for web browsing, the following ports must be allowed:
•
Outbound TCP/33001:
Allow outbound connections from the Aspera client on the TCP port (TCP/33001 by
default, when connecting to a Windows server, or on another non-default port for other server operating systems).
•
Outbound UDP/33001 (or a range, if required):
Allow outbound connections from the Aspera client on the
FASP UDP port (33001, by default).
•
Local firewall:
If you have a local firewall on the client (such as
iptables
), verify that it is not blocking your
SSH and FASP transfer ports (such as TCP/UDP 33001).
Important:
Multiple concurrent clients cannot connect to a Windows Aspera server on the same UDP port.
Similarly, multiple concurrent clients that are utilizing two or more user accounts cannot connect to a macOS,
FreeBSD, or Isilon Aspera server on the same UDP port. If connecting to these servers, you will need to allow a range
of outbound connections from the Aspera client (that have been opened incrementally on the server side, starting at
UDP/33001). For example, you may need to allow outbound connections on UDP/33001 through UDP/33010 if 10
concurrent connections are allowed by the server.
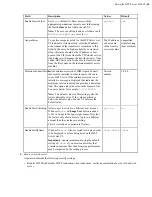
Securing Your SSH Server
Keeping your data secure is critically important. Aspera strongly recommends taking additional steps to set up and
configure your SSH server to protect against common attacks.
These steps include the following:
• Changing the TCP port.
• Configuring transfer server authentication.
Aspera also recommends restricting user access to the server, as described in the user setup instructions later in this
guide.