Redpine Signals, Inc.
Page 32
R
R
S
S
-
-
W
W
C
C
-
-
3
3
0
0
1
1
E
E
v
v
a
a
l
l
u
u
a
a
t
t
i
i
o
o
n
n
B
B
o
o
a
a
r
r
d
d
U
U
s
s
e
e
r
r
G
G
u
u
i
i
d
d
e
e
V
V
e
e
r
r
s
s
i
i
o
o
n
n
2
2
.
.
5
5
1
1
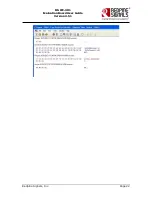
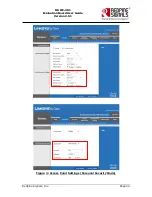
days 365 –config ./openssl.cnf
<openssl.cnf is the configuration file used to generate the certificate. A sample file
is provided at
RS.WSC.x.x.GENR.x.x.x.x.x.x\Software\Applications\Radius_server\openssl.cnf>
/* Signing the certificates with ca root certificate generated in section CA root */
openssl ca –out redpine-cert.pem –days 365 –config ./openssl.cnf –infiles redpine-
req.pem
Finally concatenate the redpine-key.pem, redpine-cert.pem cacert.pem
cat redpine-key.pem >> redpine-cert.pem >> cacert.pem.
File redpine-key.pem is the new certificate.
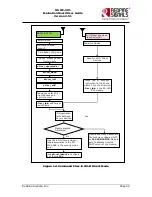
Create Encrypted Certificate
mkdir new_certs
cd new_certs/
mkdir sslcert
chmod 0700 sslcert
cd sslcert
mkdir certs private
echo '100001' >serial
touch certindex.txt
vi openssl.cnf
/* CA root */
openssl req -new -x509 -extensions v3_ca -keyout private/cakey.pem -out
cacert.pem -days 365
-config ./openssl.cnf
/*Encrypt Private Key - use this encrypted key (private/cakey1.pem ) in
openssl.cnf*/
openssl pkcs8 -in private/cakey.pem -topk8 -out private/cakey1.pem
/* Certificates Request */
openssl req -new -nodes -out redpine-req.pem -keyout private/redpine-key.pem -
days 365 -config
./openssl.cnf
/* Signing the certificates with ca root certificate generated in section CA root */
openssl ca -out redpine-cert.pem -days 365 -config ./openssl.cnf -infiles redpine-
req.pem /*Encrypt Key*/