7
IPsec VPN
125
ESP (Encapsulating Security Payload)
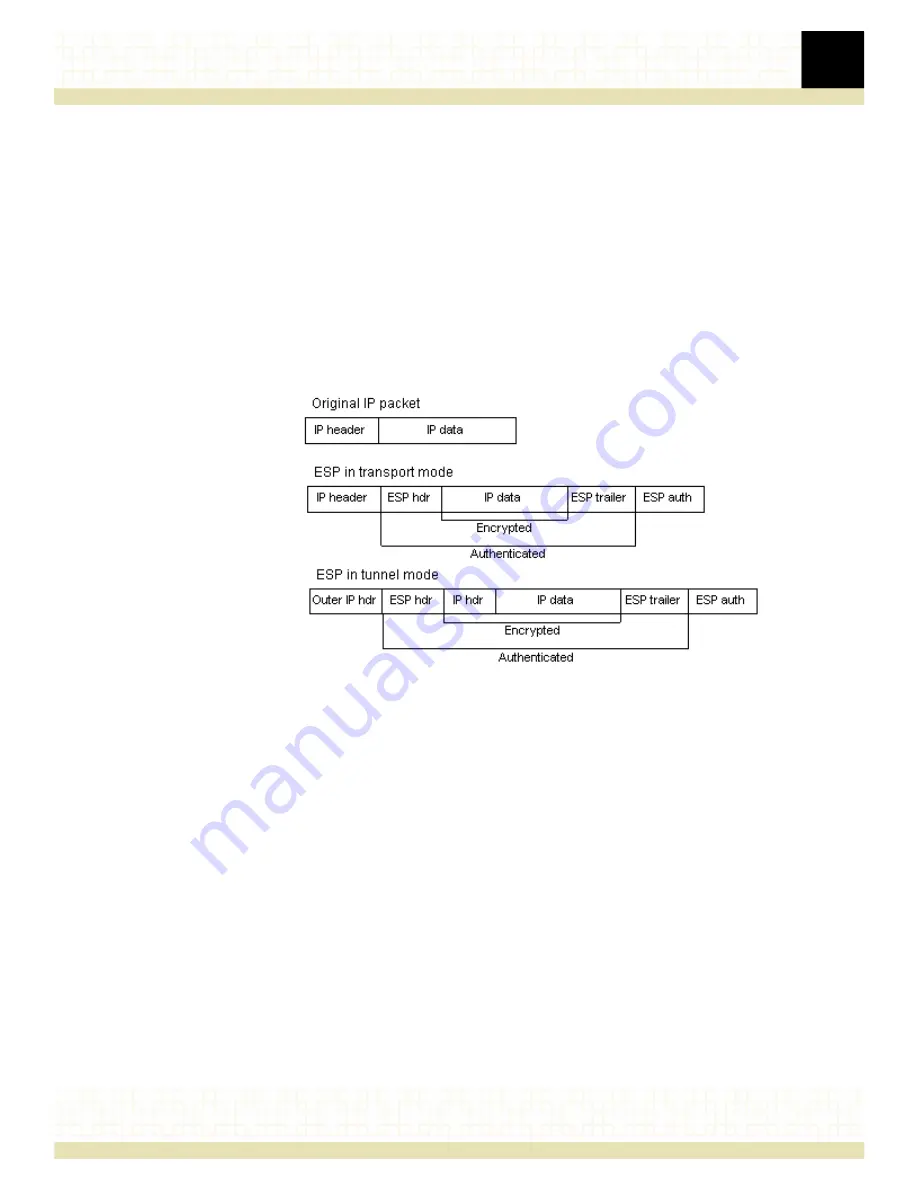
The
ESP
protocol
inserts
an
ESP
header
after
the
original
IP
header,
in
tunnel
mode,
the
ESP
header
is
inserted
after
the
outer
header,
but
before
the
original,
inner
IP
header.
All
data
after
the
ESP
header
is
encrypted
and/or
authenticated.
The
difference
from
AH
is
that
ESP
also
provides
encryption
of
the
IP
packet
whereas
AH
does
not.
The
authentication
phase
also
differs
in
that
ESP
only
authenticates
the
data
after
the
ESP
header
and
the
outer
IP
header
is
left
unprotected.
Since
AH
protects
the
outer
IP
addresses,
it
cannot
be
used
with
NAT.
The
ESP
protocol
is
used
for
both
encryption
and
authentication
of
the
IP
packet.
It
can
also
be
used
to
do
either
encryption
only,
or
authentication
only.
Figure 9. The ESP protocol
Creating and using proposal lists
To
agree
on
the
VPN
flow
parameters,
a
negotiation
between
tunnel
peers
is
performed.
As
a
result
of
these
negotiations,
the
IKE
and
IPsec
security
associations
(SAs)
are
established.
A
proposal
list
of
supported
algorithms
is
the
starting
point
for
a
negotiation.
Each
entry
in
the
list
defines
parameters
for
a
supported
algorithm
that
the
VPN
tunnel
end
point
device
is
capable
of
supporting
(the
shorter
term
tunnel
endpoint
will
also
be
used
in
this
manual).
The
initial
negotiation
attempts
to
agree
on
a
set
of
algorithms
that
the
devices
at
either
end
of
the
tunnel
can
both
support.
There
are
two
types
of
proposal
lists,
IKE
proposal
lists
and
IPsec
proposal
lists.
IKE
lists
are
used
during
IKE
Phase
‐
1
(IKE
Security
Negotiation),
while
IPsec
lists
are
using
during
IKE
Phase
‐
2
(IPsec
Security
Negotiation).
















































