CY8CKIT-064S0S2-4343W PSoC 64 Standard Secure – AWS Wi-Fi BT Pioneer Kit Guide, Doc. # 002-30680 Rev. *B
28
Provisioning Overview for PSoC 64 Standard Secure - AWS MCU’s
For evaluation purposes, the Secure Boot SDK provides the following assets to easily provision your
device:
1. A development cy_auth JWT token; this authorizes a development HSM keypair which is used by
your PC to provision the chip.
2. A development rot_auth JWT token; this authorizes a development RoT keypair which can be
used to sign your assets, such as image keys and policies.
In addition, the SDK provides tools to do the following:
1. Generate image keys
2. Form provisioning packets
3. Scripts to run the entrance exam and provisioning process on your development PC
Once the chip has been provisioned with the Public Image key, it will only boot images signed by the
associated Private key. Optionally, the image can be encrypted if the Boot and Upgrade policy
specifies it.
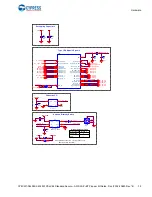
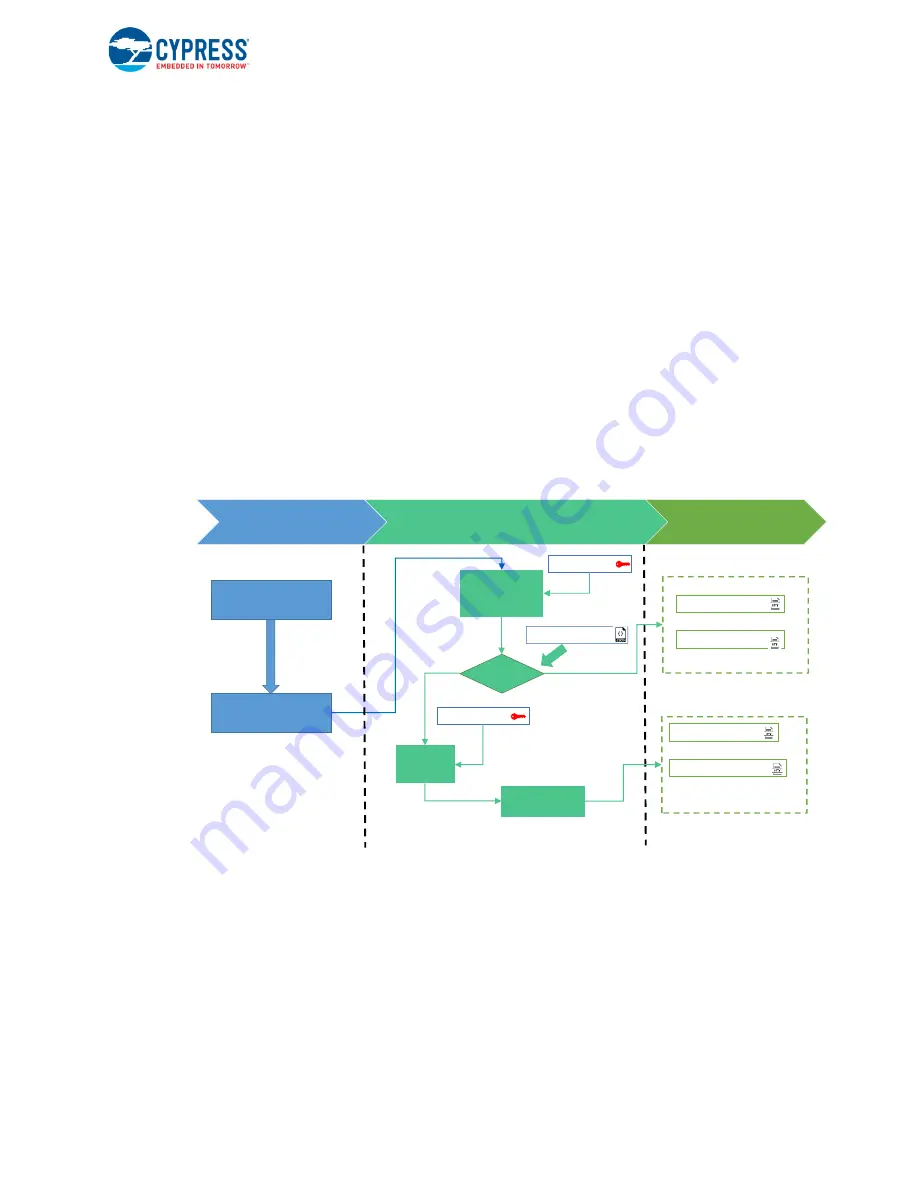
The signing and encryption process is a post build script provided by the Secure Boot SDK. The
build and encrypt/signing flow for a CY8CKIT-064S0S2-4343W target using the ModusToolbox make
process is shown below.
Figure 3-2. Build and Encrypt/Signing Flow
Standard ModusToolBox
build flow
Output HEX file
Image private key
Boot&Upgrade Policy
ECDSA signature
with Image
private key
1
Build
Encrypt/Sign
Output
example.hex
example_upgrade.hex
Signed, Boot image(Slot#0)
Signed, Upgrade image(Slot#1)
example.hex
example_enc_upgrade.hex
Signed, Boot image(Slot#0)
Encrypted & Signed, Upgrade Image(Slot#1)
Encrypt = Yes
Encrypt = No
1
Standard MCUBoot Signing
2
Custom CySecureBootloader Signing
Image AES128 key
Encrypt?
Yes
Encrypt
Upgrade
Image
No
Re-sign image
2