9.1 Description
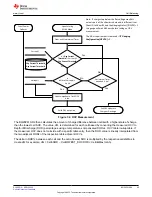
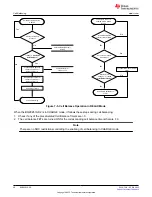
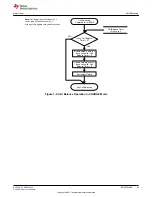
There are three levels of secured operation within the device. To switch between the levels, different operations
are needed with different keys. The three levels are SEALED, UNSEALED, and FULL ACCESS. The device also
supports SHA-1 HMAC authentication with the host system.
9.2 SHA-1 Description
As of March 2012, the latest revision is FIPS 180-4. SHA-1, or secure hash algorithm, is used to compute a
condensed representation of a message or data, also known as hash. For messages < 2
64
, the SHA-1 algorithm
produces a 160-bit output called a digest.
In a SHA-1 one-way hash function, there is no known mathematical method of computing the input given, only
the output. The specification of SHA-1, as defined by FIPS 180-4, states that the input consists of 512-bit blocks
with a total input length less than 264 bits. Inputs that do not conform to integer multiples of 512-bit blocks are
padded before any block is input to the hash function. The SHA-1 algorithm outputs the 160-bit digest.
The device generates a SHA-1 input block of 288 bits (total input = 160-bit m 128-bit key). To complete
the 512-bit block size requirement of the SHA-1 function, the device pads the key and message with a 1,
followed by 159 0s, followed by the 64 bit value for 288 (000...00100100000), which conforms to the pad
requirements specified by FIPS 180-4.
Detailed information about the SHA-1 algorithm can be found here:
1.
2.
http://csrc.nist.gov/publications/fips
3.
www.faqs.org/rfcs/rfc3174.html
9.3 HMAC Description
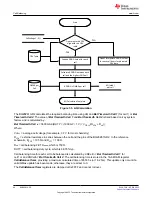
The SHA-1 engine calculates a modified HMAC value. Using a public message and a secret key, the HMAC
output is considered to be a secure fingerprint that authenticates the device used to generate the HMAC.
To compute the HMAC: Let H designate the SHA-1 hash function, M designate the message transmitted to the
device, and KD designate the unique 128-bit Unseal/Full Access/Authentication key of the device. HMAC(M) is
defined as:
H[KD || H(KD || M)], where || symbolizes an append operation.
The message, M, is appended to the unseal/full access/authentication key, KD, and padded to become the input
to the SHA-1 hash. The output of this first calculation is then appended to the unseal/full access/authentication
key, KD, padded again, and cycled through the SHA-1 hash a second time. The output is the HMAC digest
value.
Chapter 9
Device Security
Device Security
SLUUCO0 – APRIL 2022
BQ28Z610-R2
53
Copyright © 2022 Texas Instruments Incorporated