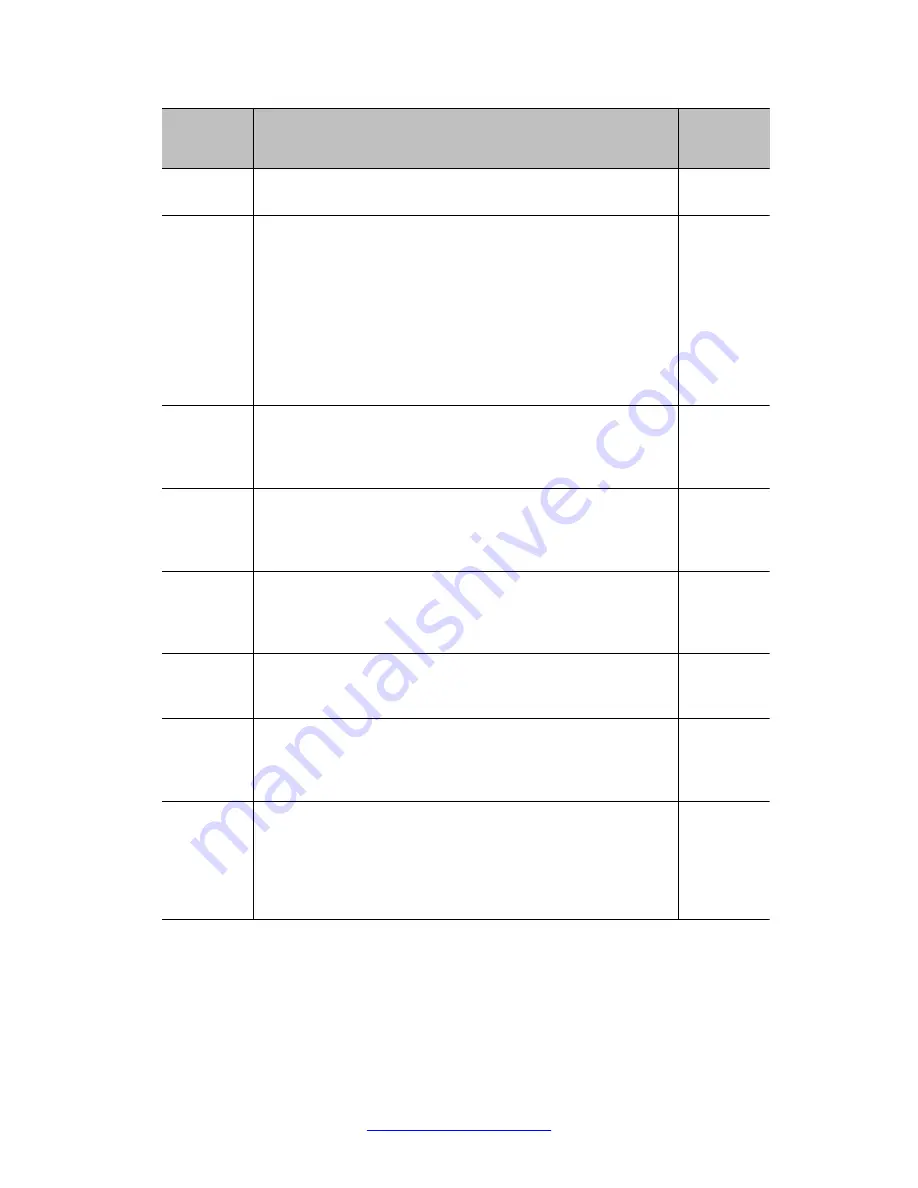
Algorithm
How it is used by the HSM module
Used in
FIPS 140-1
Mode?
Encrypt and Decrypt services are not available for this algorithm
in FIPS mode because keys are entered in plaintext.
RSA
Signature/
Verification
Generation and verification of digital signatures using the RSA
algorithm, in accordance with the PKCS #1 specification. Keys
pairs of modulus size in the range 192 through 1024 bits, in 64
bit increments. Note: The message digest operation of the
digital signature and verification function is performed outside
of the cryptographic boundary for performance reasons. After
the digest is computed outside the module, the module formats
and pads the message digest according to the PKCS #1
standard and then uses the RSA algorithm to compute the
digital signature.
Yes
SHA-1
Hashing of host-provided data. Hashing for the purpose of
verifying the RSA digital signature of a firmware image. Hashing
a 3DES key for the purpose of checking its integrity after it is
split and then the corresponding shares combined.
Yes
MD5
The module provides services to compute an MD5 message
digest. As this algorithm is not FIPS-approved, the
corresponding services are not available in the FIPS 140-1
Mode.
No
HMAC
(SHA-1)
The module provides a service to compute HMAC using SHA-1.
As currently implemented, the service requires the MAC key to
be input unencrypted through the PCI interface, and therefore
this service is not available in the FIPS 140-1 Mode.
No
HMAC
(MD5)
The module provides a service to compute HMAC using MD5.
Because MD5 is not a FIPS-approved algorithm, this service is
not available in the FIPS 140-1 Mode.
No
RC4
The module provides services for encryption/decryption with
RC4. Because RC4 is not a FIPS-approved algorithm, the
corresponding services are not available in the FIPS 140-1
Mode.
No
DSA
The module provides services for generating and verifying DSA
signatures. As currently implemented, the private key for
signature generation must be input through the PCI interface.
Therefore, this algorithm is not available in the FIPS 140-1
Mode. Keys pairs of modulus size in the range 512 through 1024
bits, in 64 bit increments.
No
HSM Security Policy
222 User Guide
April 2013
Comments? infodev@avaya.com
Summary of Contents for 3050-VM
Page 1: ...User Guide Avaya VPN Gateway Release 9 0 NN46120 104 Issue 04 04 April 2013 ...
Page 4: ...4 User Guide April 2013 Comments infodev avaya com ...
Page 12: ...12 User Guide April 2013 ...
Page 20: ...New in this release 20 User Guide April 2013 Comments infodev avaya com ...
Page 30: ...Introducing the VPN Gateway 30 User Guide April 2013 Comments infodev avaya com ...
Page 36: ...Introducing the ASA 310 FIPS 36 User Guide April 2013 Comments infodev avaya com ...
Page 74: ...Upgrading the AVG Software 74 User Guide April 2013 Comments infodev avaya com ...
Page 86: ...Managing Users and Groups 86 User Guide April 2013 Comments infodev avaya com ...
Page 130: ...The Command Line Interface 130 User Guide April 2013 Comments infodev avaya com ...
Page 162: ...Supported Ciphers 162 User Guide April 2013 Comments infodev avaya com ...
Page 212: ...Syslog Messages 212 User Guide April 2013 Comments infodev avaya com ...
Page 242: ...Definition of Key Codes 242 User Guide April 2013 Comments infodev avaya com ...
Page 259: ...Creating a Port Forwarder Authenticator User Guide April 2013 259 ...
Page 266: ...Using the Port Forwarder API 266 User Guide April 2013 Comments infodev avaya com ...
Page 274: ...X 509 274 User Guide April 2013 Comments infodev avaya com ...
















































