Chapter 7. Using the Online Certificate Status Protocol Responder
188
6. Verify that the CA is properly connected to the OCSP responder; see
Section 7.2.1, “Verify
Certificate Manager and Online Certificate Status Manager Connection”
.
7.2. Identifying the CA to the OCSP Responder
Before a CA is configured to publish CRLs to the Online Certificate Status Manager, the CA must be
identified to the Online Certificate Status Manager by storing the CA signing certificate in the internal
database of the Online Certificate Status Manager. The Certificate Manager signs CRLs with the
key pair associated with this certificate; the Online Certificate Status Manager verifies the signature
against the stored certificate.
NOTE
If a CA within the security domain is selected when the Online Certificate Status Manager
is configured, there is no extra step required to configure the Online Certificate Status
Manager to recognize the CA; the CA signing certificate is automatically added and
trusted in the Online Certificate Status Manager's certificate database. However, if a non-
security domain CA is selected, then the CA signing certificate must be manually added to
the certificate database after the Online Certificate Status Manager is configured.
It is not necessary to import the certificate chain for a CA which will publish its CRL to the Online
Certificate Status Manager. The only time a certificate chain is needed for the OCSP service is if the
CA connects to the Online Certificate Status Manager through SSL authentication when it publishes its
CRL. Otherwise, the Online Certificate Status Manager does not need to have the complete certificate
chain.
However, the Online Certificate Status Manager must have the certificate which signed the CRL, either
a CA signing certificate or a separate CRL signing certificate, in its certificate database. The OCSP
service verifies the CRL by comparing the certificate which signed the CRL against the certificates in
its database, not against a certificate chain. If both a root CA and one of its subordinate CAs publish
CRLs to an Online Certificate Status Manager, the Online Certificate Status Manager needs the CA
signing certificate of both CAs.
To import the CA or CRL signing certificate which is used to sign the certificates the CA is publishing to
the Online Certificate Status Manager, do the following:
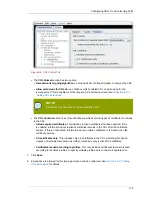
1. Get the Certificate Manager's base-64 CA signing certificate from the end-entities page of the CA.
2. Open the Online Certificate Status Manager agent page. The URL has the format
https://
hostname:SSLport
/ocsp/agent/ocsp
.
3. In the left frame, click
Add Certificate Authority
.
4. In the form, paste the encoded CA signing certificate inside the text area labeled
Base 64
encoded certificate (including the header and footer)
.
5. To verify that the certificate is added successfully, in the left frame, click
List Certificate
Authorities
.
The resulting form should show information about the new CA. The
This Update
,
Next Update
, and
Requests Served Since Startup
fields should show a value of zero (0).
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...