Chapter 12. Editing Configuration in the CS.cfg File
292
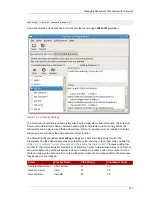
a. Create a temporary directory and copy the CGI scripts into it.
mkdir /tmp/sow
cp /usr/share/pki/tps/cgi-bin/sow/*.cgi /tmp/sow
b. Create a temporary directory and copy the CGI scripts into it.
c. Edit the CGI files, using the appropriate server root for the TPS instance. For example:
pushd /tmp/sow
for i in `ls *.cgi`; do
sed -i 's/\[SERVER_ROOT\]/\/var\/lib\/pki-tps-old/g' $i
done
cp -f *.cgi /var/lib/pki-tps-old/cgi-bin/sow
popd
d. Remove the temporary directory.
rm -f /tmp/sow
e. Set the proper file owner and permissions for the files.
chown pkiuser: /var/lib/pki-tps-old/cgi-bin/sow/*.cgi
chmod 755 /var/lib/pki-tps-old/cgi-bin/sow/*.cgi
6. If the security officer scripts have been customized, then the files need to be updated so that they
properly run under
mod_perl::PerlRun
instead of
mod_cgi
.
The primary change is to replace any relative file paths with full paths. For example, replace this
line:
require "
./cfg.pl
"
With:
require "
/var/lib/pki-tps/cgi-bin/sow/cfg.pl
"
Other changes may be needed to eliminate warnings in the error_log.
7. Create a new HTTP init.d file for the instance. THe easiest way to do this is to create a temporary
TPS instance, copy its init.d file, and then edit it to point to the original instance.
a. Run
pkicreate
to create a TPS instance.
b. Copy the new instance's init.d file.
cp /etc/init.d/pki-temp-tps /tmp/pki-tps-old
c. Replace the new instance name with the original TPS instance name. For example:
sed -i 's/pki-temp-tps/pki-tps-old/g' /tmp/pki-tps-old
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...