Chapter 15. Configuring Subsystem Logs
366
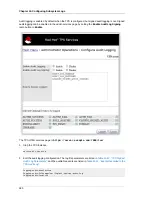
[Sat Jun 20 16:28:09 2009] [debug] nss_engine_init.c(594): Enabling SSL3
[Sat Jun 20 16:28:09 2009] [debug] nss_engine_init.c(599): Enabling TLS
[Sat Jun 20 16:28:09 2009] [debug] nss_engine_init.c(770): Configuring permitted SSL ciphers
[-des,-desede3,-rc2,-rc2export,-rc4,-rc4rsa_3des_sha,-rsa_des_rsa_des_sha,-
rsa_null_md5,-rsa_null_sha,-rsa_rc2_rsa_rc4_128_md5,-rsa_rc4_128_sha,-rsa_rc4_40_md5,-
rsa_rc4_56_sha,-fortezza,-fortezza_rc4_128_sha,-fortezza_null,-fips_dfips_3des_sha,-
rsa_aes_128_sha,-rsa_aes_2ecdhe_ecdsa_aes_256_sha]
[Sat Jun 20 16:28:09 2009] [info] Using nickname Server-Cert cert-pki-tps.
Example 15.5. TPS Error Log Snippet
15.2.5. Installation Logs
All six subsystems keep an install log.
Every time a subsystem is created either through the initial installation or creating additional instances
with
pkicreate
, an installation file with the complete debug output from the installation, including
any errors and, if the installation is successful, the URL and PIN to the configuration interface for
the instance. The file is created in the default log directory,
/var/log
, with a name in the form
instance_ID
-install.log
.
[
date time
] [debug]
message
Each line in the install log follows a step in the installation process.
[2009-05-19 09:30:30] [debug] Processing PKI files and symbolic links for '/var/lib/pki-
ra' ...
[2009-05-19 09:30:31] [debug] Processing PKI security databases for '/var/lib/pki-ra' ...
[2009-05-19 09:30:31] [debug] Processing PKI security modules for '/var/lib/pki-ra' ...
[2009-05-19 09:30:31] [debug] Attempting to add hardware security modules to system if
applicable ...
[2009-05-19 09:30:31] [debug] module name: lunasa lib: /usr/lunasa/lib/
libCryptoki2.so DOES NOT EXIST!
[2009-05-19 09:30:31] [debug] module name: nfast lib: /opt/nfast/toolkits/pkcs11/
libcknfast.so DOES NOT EXIST!
[2009-05-19 09:30:31] [debug] Restorecon file context for /usr/share/pki
[2009-05-19 09:30:32] [debug] Restorecon file context for /etc/rc.d/init.d/pki-ra
[2009-05-19 09:30:33] [debug] Restorecon file context for /var/lib/pki-ra
[2009-05-19 09:30:33] [debug] Restorecon file context for /var/log/pki-ra
[2009-05-19 09:30:34] [debug] Restorecon /etc/pki-ra
[2009-05-19 09:30:34] [debug] Restorecon file context for /usr/sbin/httpd.worker
[2009-05-19 09:30:34] [debug] Setting selinux context pki_ra_port_t for 12890
[2009-05-19 09:30:39] [debug] Setting 'pki-ra' runlevel to '-'
[2009-05-19 09:30:39] [debug] Setting 'pki-ra' start priority to '86'
[2009-05-19 09:30:39] [debug] Setting 'pki-ra' stop priority to '14'
[2009-05-19 09:30:39] [debug] Registered 'pki-ra' with '/sbin/chkconfig'.
[2009-05-19 09:30:54] [log] Configuration Wizard listening on
http://server.example.com:12888/ra/admin/console/config/login?pin=U3PXGwMJrcDPj4RrmDdK
[2009-05-19 09:30:54] [log] After configuration, the server can be operated by the command:
/sbin/service pki-ra start | stop | restart
Example 15.6. RA Install Log
15.2.6. Apache and Tomcat Error and Access Logs
The CA, RA, DRM, OCSP, and TKS subsystems use a Tomcat web server instance for their agent and
end-entities' interfaces. The TPS and RA subsystems use an Apache web server.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...