16
Step Command
Remarks
4.
Use the device to log in to a
Telnet server.
•
Log in to an IPv4 Telnet server:
telnet
remote-host
[
service-port
] [
source
{
interface
interface-type
interface-number
|
ip
ip-address
} ]
•
Log in to an IPv6 Telnet server:
telnet
ipv6
remote-host
[
-i
interface-type
interface-number
]
[
port-number
]
Use either command.
Logging in through SSH
SSH offers a secure approach to remote login. By providing encryption and strong authentication, it
protects devices against attacks such as IP spoofing and plain text password interception. You can use an
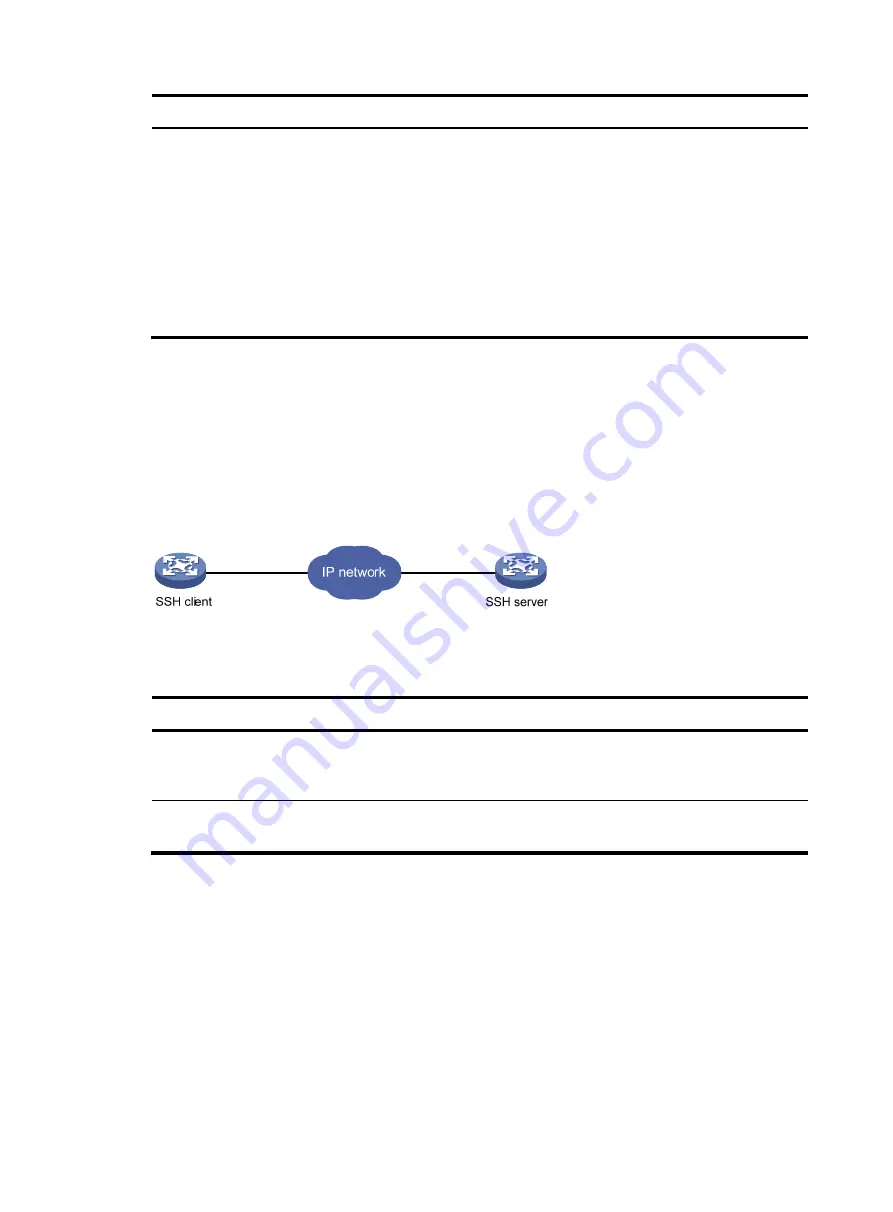
SSH client to log in to the device operating as an SSH server for remote management, as shown in
. You can also use the device as an SSH client to log in to an SSH server.
Figure 7
SSH login diagram
shows the SSH server and client configuration required for a successful SSH login.
Table 7
SSH server and client requirements
Device role
Requirements
SSH server
Assign an IP address to a Layer 3 interface, and make sure the interface and
the client can reach each other.
Configure the authentication mode and other settings.
SSH client
If a host operates as an SSH client, run the SSH client program on the host.
Obtain the IP address of the Layer 3 interface on the server.
To control SSH access to the device operating as an SSH server, configure authentication and user
privilege level for SSH users. By default, password authentication is adopted for SSH login, but no login
password is configured. To allow SSH access to the device after you enable the SSH server, you must
configure a password.
Configuring the SSH server on the device
When scheme authentication is used, you can choose to configure the command authorization and
command accounting functions.
If command authorization is enabled, a command is available only if the user has the commensurate user
privilege level and is authorized to use the command by the AAA scheme.