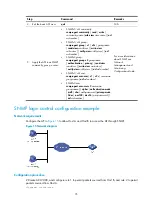
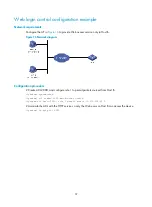
27
<AP> system-view
[AP] pki entity en
[AP-pki-entity-en] common-name http-server1
[AP-pki-entity-en] fqdn ssl.security.com
[AP-pki-entity-en] quit
# Create a PKI domain, specify the trusted CA as
new-ca
, the URL of the server for certificate
request as
http://10.1.2.2/certsrv/mscep/mscep.dll
, authority for certificate request as
RA
, and
the entity for certificate request as
en
.
[AP] pki domain 1
[AP-pki-domain-1] ca identifier new-ca
[AP-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.dll
[AP-pki-domain-1] certificate request from ra
[AP-pki-domain-1] certificate request entity en
[AP-pki-domain-1] quit
# Create RSA local key pairs.
[AP] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Press CTRL+C to abort.
Input the bits of the modulus[default = 1024]:
Generating Keys...
+++++
++++++++++++++
+++++++++++++
++++++++
# Retrieve the CA certificate.
[AP] pki retrieval-certificate ca domain 1
The trusted CA's finger print is:
MD5 fingerprint:3352 F952 0D8E FDF8 AB98 08ED 11D3 B005
SHA1 fingerprint:1628 60B1 367B D012 D08C 85D3 8D2F 5D10 1F9D 4B39
Is the finger print correct?(Y/N): y
# Request a local certificate for the AP through SCEP.
[AP] pki request-certificate domain 1
# Create SSL server policy
myssl
, specify PKI domain 1 for the SSL server policy, and enable
certificate-based SSL client authentication.
[AP] ssl server-policy myssl
[AP-ssl-server-policy-myssl] pki-domain 1
[AP-ssl-server-policy-myssl] client-verify enable
[AP-ssl-server-policy-myssl] quit
# Create certificate attribute group
mygroup1
and configure a certificate attribute rule for it,
specifying that the distinguished name in the subject name includes the string of
new-ca
.
[AP] pki certificate attribute-group mygroup1
[AP-pki-cert-attribute-group-mygroup1] attribute 1 issuer-name dn ctn new-ca
[AP-pki-cert-attribute-group-mygroup1] quit