aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
User Authentication Process
3.5.4.1
Static Password Verification
Static Password Verification calls on the Static Password defined in the DIGIPASS User Account record. This
password is also used for other purposes (see section
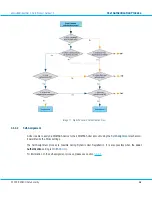
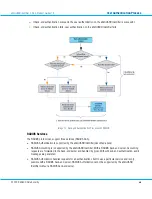
Static Password authentication passes through the steps shown in the image below and described here, cross-
referencing the numbers in the image:
1.
If a User account does not exist, the request is passed on to the Dynamic User Registration check in step 5. If
a User account exists, the request continues to the User account check in step 2.
2.
If a static password is not set in the User account, the request is passed on to the back-end authentication
check in step 6. If a static password is set in the User account, the request continues to local authentication
(step 3).
3.
If local authentication with the static password is not successful, the request is passed on to the back-end
authentication availability check in step 6. If local authentication is successful, the request continues to the
Policy check in step 4.
4.
If local authentication is successful and back-end authentication is not mandatory, the User is authenticated.
If local authentication is successful, but back-end authentication is mandatory, the request is passed on to
the back-end authentication availability check in step 6. (For more information on Policy settings for back-
end authentication, please see section
)
5.
If DUR is not permitted, authentication fails. If DUR is permitted, the request is passed on to the back-end
authentication availability check in step 6.
6.
If back-end authentication is not available, authentication fails. If back-end authentication is available, the
request is passed on to step 7.
7.
If back-end authentication is not successful, authentication fails; if back-end authentication succeeds, the
User is authenticated.
Note:
If the
Local Authentication
setting is DIGIPASS Only, static password verification on its own is
not permitted. An OTP must be used during login. This is possible using Self-Assignment (see
the following section and section
©
2009 VASCO Data Security
38