aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
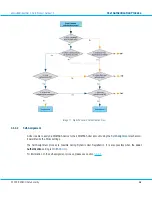
User Authentication Process
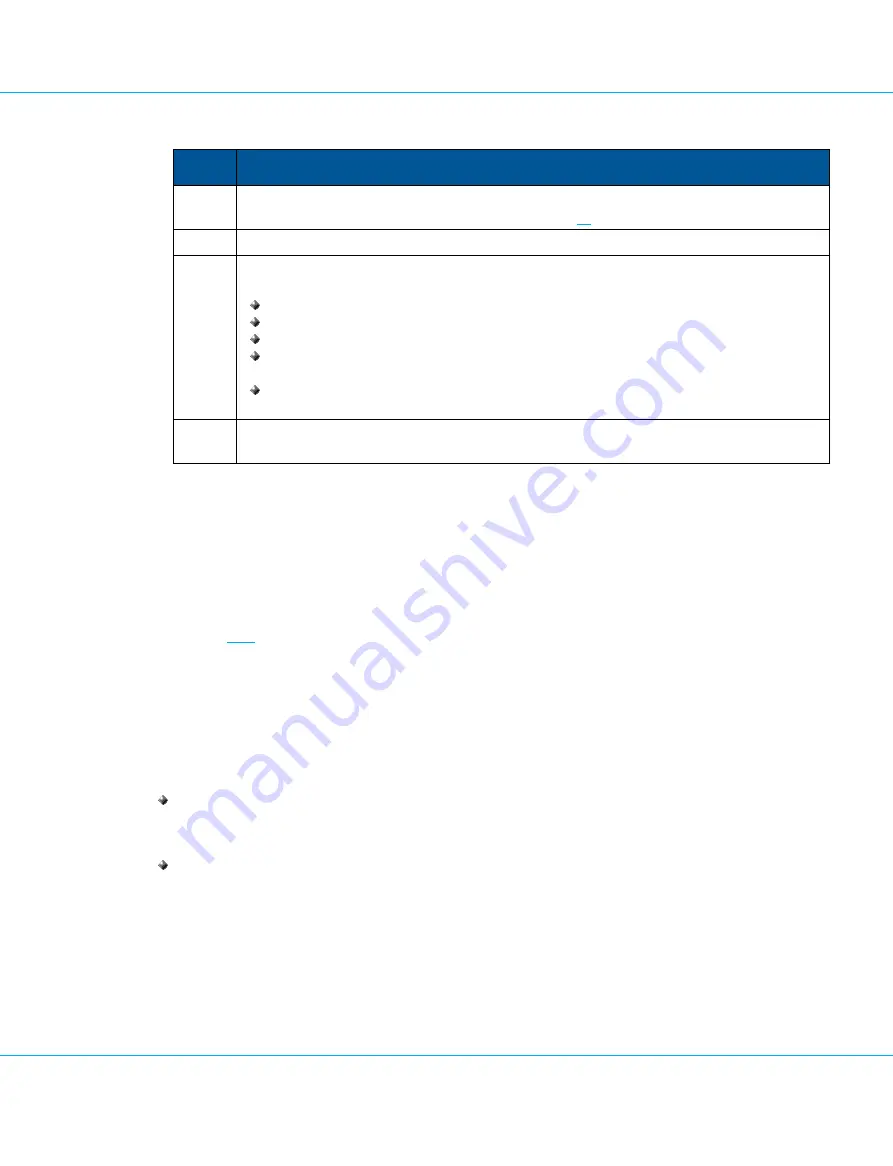
Table 2: Values for Back-end Authentication Setting
Setting
Explanation
Default
Back-end authentication is handled as configured in settings inherited from the parent policy. More
information on policies and inheritance can be found in section
None
The aXsGUARD Identifier does not use back-end authentication.
If needed
Back-end authentication is only used in situations where Local Authentication is not sufficient and to support
certain features:
Dynamic User Registration
Self-Assignment
Password Autolearn
Requesting a Challenge or Virtual DIGIPASS One Time Password (OTP), when the Request Method
includes a Password
Static password authentication, when verifying a Virtual DIGIPASS password-OTP combination or during
the Grace Period
Always
The aXsGUARD Identifier uses back-end authentication for every authentication request. This is necessary if
you require RADIUS attributes for each login.
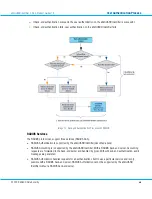
3.6.3
Back-end Authentication and Static Password
The table above lists scenarios supported by back-end authentication. To use these scenarios requires a DIGIPASS
User Account static password. In this section, we explain options for manipulating the static password field during
the authentication process. For more information on DIGIPASS User Accounts and static password handling, please
see section
3.6.3.1
Stored Password Proxy
When the
Stored Password Proxy
setting is enabled in the Policy, and the User authenticates using a DIGIPASS
OTP only, the aXsGUARD Identifier retrieves the Stored Static Password from the DIGIPASS User account, which
can then be used:
for authentication towards a back-end server. This means that the User does not need to type in the static
password at each login; they only need enter the OTP. A practical use of this setup is forwarding RADIUS
attributes from a back-end server (see section below).
to support Password Replacement. Back-end authentication is used to learn the static password so that it can
be replayed to the host system (e.g. Outlook Web Access) when a successful OTP is given (see section below).
However, if the User enters a static password before their OTP, the static password entered takes precedence over
the Stored Static Password. In this case, the Stored Static Password is not used at all for the login.
When the
Stored Password Proxy
setting is
not
enabled in the Policy, the Stored Static Password is not used for
back-end authentication. If back-end authentication is required for a login, the User must enter the static
password, before the OTP, if an OTP is also used. Similarly, if there is a host system that requires a static
password to be returned, the User must enter the static password.
©
2009 VASCO Data Security
41