| Authentication and Authorization |
290
•
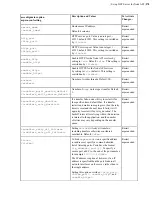
Transfer Tokens:
A transfer token authorizes specific content uploads to a destination or content downloads
from a remote source. Transfer-token-based authorization is generally used for FASP transfers initiated through
Aspera web applications, such as IBM Aspera Faspex, IBM Aspera Shares, and IBM Aspera Application for
Microsoft SharePoint, but can be used in place of SSH authentication for other types of Aspera products. For more
information, see
Transfer Token Creation (Node API)
on page 291 and
Transfer Token Generation (astokengen)
on page 293.
•
Basic Tokens:
An Aspera basic token is created from an access key ID and secret, which authorizes a transfer user
access to a specific area of a storage and authenticates that user to the storage. Basic tokens are less restrictive than
transfer tokens. They can be used to transfer with any Aspera server that supports access keys (all but IBM Aspera
on Cloud). For more information, see
on page 304.
•
Bearer Tokens:
A bearer token is created from an access key ID, access key secret, and an SSL private-public key
pair. Bearer token authentication is required for transfers to and from IBM Aspera on Cloud, but can be used for
transfers with all other Aspera servers, too. For more information, see
on page 305.
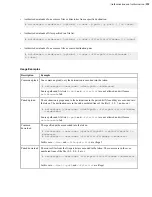
Require Token Authorization: Set from the Command Line
When transfer users or groups are configured to require token authorization, only transfers initiated with a valid token
(transfer token, basic token, or bearer token) are allowed to transfer to or from the server. Token authorization can be
set independently for incoming transfers and outgoing transfers.
The following examples use a transfer user called
aspera_user_1
.
1.
Choose or create the transfer user on the server.
The user should not have a password. If the system does not allow this, create a very large password.
2.
Set the IBM Aspera Connect public SSH key as an authorized key for the transfer user and ensure that they own
the file.
a) Create the
.ssh
directory in the user's home folder.
# mkdir /home/aspera_user_1/.ssh/
b) Copy the Connect public SSH key into
.ssh
and rename it
authorized_keys
(or append the public key
to
authorized_keys
if the file already exists).
# cp /opt/aspera/var/aspera_tokenauth_id_rsa.pub /home/
aspera_user_1/.ssh/authorized_keys
c) Ensure that
.ssh
and
.ssh/authorized_keys
are owned by the user.
# chown -R aspera_user_1:aspera_user_1 /home/aspera_user_1/.ssh
# chmod 600 /home/aspera_user_1/.ssh/authorized_keys
# chmod 700 /home/aspera_user_1
# chmod 700 /home/aspera_user_1/.ssh
3.
To require token authorization for uploads and downloads, and to set the token encryption key, run the following
command:
# asconfigurator -x
"set_user_data;user_name,aspera_user_1;authorization_transfer_in_value,token;authorization_transfer_out_value,token;token_encryption_key,
key
"
Aspera recommends that the
key
be a random string of at least 20 characters. This command creates the following
text in
aspera.conf
:
<user>
<name>aspera_user_1</name>
<authorization>
<transfer>
<in>