| Appendix |
334
or for Linux systems that use
init.d
:
# service asperahttpd restart
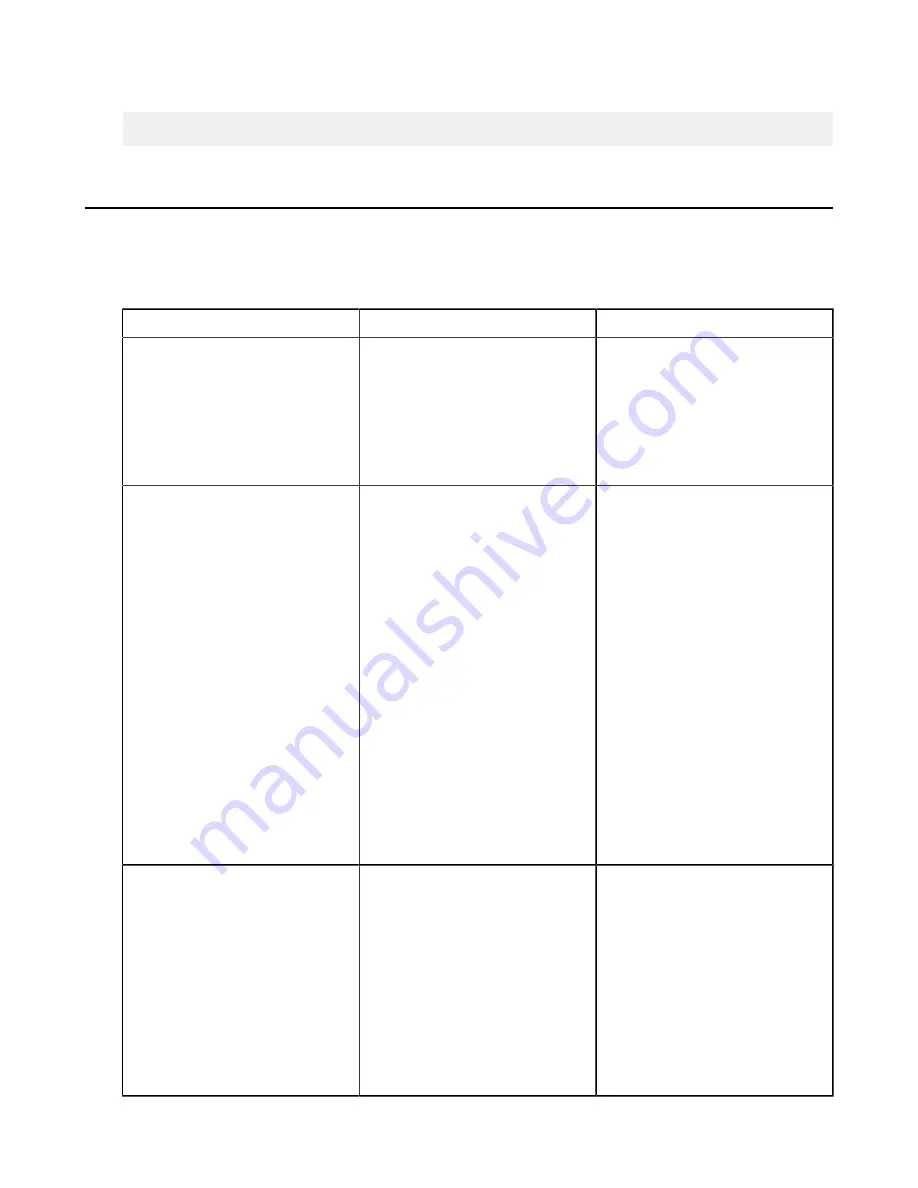
Docroot vs. File Restriction
A transfer user's access to the server's file system can be restricted by configuring a docroot or a file restriction.
Though similar, certain Aspera features require that the transfer user have a file restriction rather than a docroot.
Note:
A configuration (global, group, or user) can have a docroot or a file restriction; configurations with both are
not supported.
Docroot
File Restriction
Required for
• Server-side encryption-at-rest
(docroot in URI format)
• Connecting the node to IBM
Aspera Faspex, IBM Aspera
Shares, IBM Aspera Console,
or IBM Aspera Application for
Microsoft SharePoint
• Complex file-system access rules
• Creating access keys with the
Node API
• Connecting the node to IBM
Aspera on Cloud
Syntax
An absolute pathname that can
include a substitutional string.
Supported strings:
•
$(name)
•
$(home)
The pathname can be in URI format;
special characters must be URL-
encoded.
A set of file system filters that use
"*" as a wildcard and "!" to indicate
"exclude". Paths are in URI format;
special characters in a URI must be
URL-encoded.
Access to a file is rejected unless the
file matches the restrictions, which
are processed in the following order:
• If a restriction starts with "!", the
user is not allowed to access any
files that match the rest of the
restriction.
• If a restriction does not start with
"!", the user can access any file
that matches the filter.
• If one or more restrictions do not
start with "!", the user can access
any file that matches any one of
the no-"!" restrictions.
Examples
• As an absolute path:
/docs
• With a substitutional string:
/users/$(name)
• As a URI:
s3://s3.amazonaws.com/
my_bucket
or
file:///docs
• For a specific folder:
• For the drive root:
• For ICOS-S3 storage:
s3://my_vault/*
• To exclude access to key files:
!*.key
164