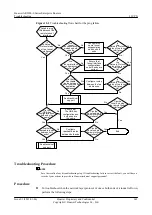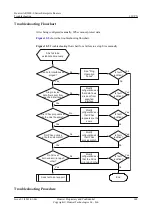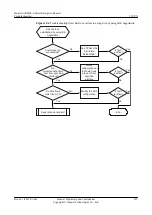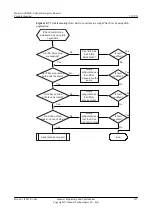
Field
Check Standard and Operation
ESP Protocol The authentication algorithm and encryption algorithm used by the ESP
protocol at both ends must be the same. If not, run the
esp authentication-
algorithm
[
md5
|
sha1
] command to change the authentication algorithm
or run the
esp encryption-algorithm
[
3des
|
des
|
aes-128
|
aes-192
|
aes-256
] command to change the encryption algorithm.
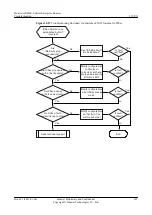
If the settings of IPSec protocols at both ends are the same, go to step 5.
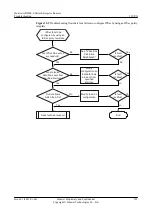
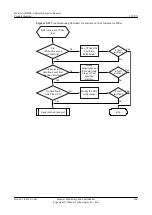
Step 5
Check whether the settings of IPSec policies at both ends of the IPSec tunnel match.
Check
Item
Check Standard and Operation
IPSec
negotiati
on mode
Run the
display ipsec policy
brief
command to view the
Mode
field. If the IPSec
negotiation modes at both ends are different, run the
ipsec policy
isakmp
command to change the IPSec negotiation modes to be the same.
Diffie-
Hellman
(DH)
group
If PFS is specified on the local device, PFS must be specified on the remote device.
The two ends must use the same DH group; otherwise, IKE negotiation fails. Run
the
display ipsec policy
command to view the
Perfect Forward Secrecy
field.
If the DH groups at both ends are different, run the
pfs
{
dh-group1
|
dh-
group2
} command to change the DH groups to be the same.
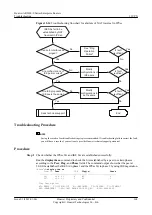
If the settings of IPSec policies at both ends of the IPSec tunnel match, go to step 6.
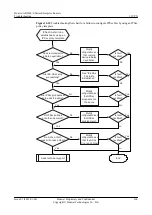
Step 6
Check whether the ACLs referenced by IPSec policies at both ends of the IPSec tunnel mirror
each other.
Run the
display acl
command on the Router. If the following information is displayed, the ACLs
referenced by IPSec policies at both ends of the IPSec tunnel mirror each other.
# Display the ACL configuration on RouterA.
<RouterA>
display acl 3101
Advanced ACL 3101, 1 rule
Acl's step is 5
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
# Display the ACL configuration on RouterB.
<RouterB>
display acl 3101
Advanced ACL 3101, 1 rule
Acl's step is 5
rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
l
If the ACLs referenced by IPSec policies at both ends of the IPSec tunnel do not mirror
each other, modify the configuration according to
Huawei AR2200-S Series Enterprise
Routers Configuration Guide - IPSec
.
l
If the ACLs referenced by IPSec policies at both ends of the IPSec tunnel mirror each other,
go to step 2.
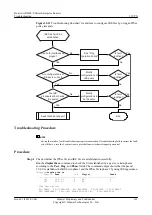
Step 7
Check whether the interfaces at both ends of the IPSec tunnel can ping each other.
Run the
undo ipsec policy
command on the interfaces of the Router at both ends of the IPSec
tunnel to delete IPSec policies. Run the
ping
command to check whether the ping operation
succeeds.
Huawei AR2200-S Series Enterprise Routers
Troubleshooting
12 VPN
Issue 01 (2012-01-06)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
356