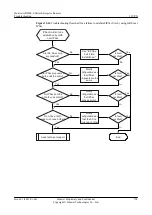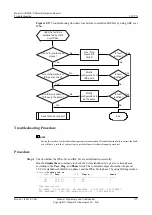
l
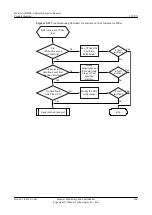
If the ACLs referenced by IPSec policies at both ends of the IPSec tunnel mirror each other,
go to step 2.
Step 7
Check whether the interfaces at both ends of the IPSec tunnel can ping each other.
Run the
undo ipsec policy
command on the Router interfaces at both ends of the IPSec tunnel
to delete IPSec policies. Run the
ping
command to check whether the ping operation succeeds.
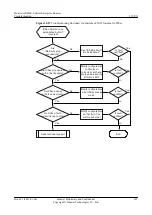
l
If the ping operation fails, check whether there are routes to the peer ends in the routing
tables at both ends according to
7.1.1 The Ping Operation Fails
.
l
If the ping operation succeeds, there are reachable routes at both ends of the IPSec tunnel.
Reconfigure the IPSec policies on interfaces at both ends, and go to step 8.
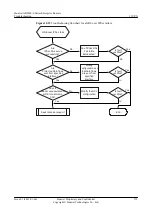
Step 8
Check whether the configurations of IKE peers are correct.
Run the
display ike peer
command to check the following fields.
Field
Check Standard and Operation
Exchange
mode
The IKE negotiation modes in phase 1 must be the same. If not, run the
exchange-mode
{
main
|
aggressive
} command to change the IKE
negotiation modes to be the same.
Negotiated
IKE version
The IKE versions must be the same. If not, run the
ike peer
command to
change the IKE versions to be the same.
Peer ip
address
Local ip
address
The peer IP address of the local end must be the same as the local IP address
of the remote end, and the local IP address of the local end must be the same
as the peer IP address of the remote end. If IP addresses of IKE peers do not
match, run the
local-address
command to change the local IP address of the
IKE peer or run the
remote-address
command to change the peer IP address
of the IKE peer.
remote-name
The remote name of the local end must be the same as the local name of the
peer end. If not, run the
remote-name
command to change the name of the
remote peer.
NOTE
The name of the remote peer is used in the following scenarios:
l
IKEv1 and the aggressive mode are used, and the name is used for authentication.
l
IKEv2 is used and the remote IKE peer ID type is name.
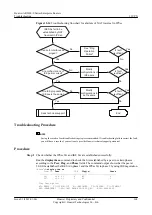
If the configurations of IKE peers are correct, go to step 9.
Step 9
Check whether the settings of IKE proposals at both ends of the IPSec tunnel are the same.
Run the
display ike proposal
command on both devices to check whether the settings of IKE
proposals at both ends of the IPSec tunnel are the same.
l
If the settings of IKE proposals at both ends of the IPSec tunnel are different, reconfigure
IKE proposals according to
Huawei AR2200-S Series Enterprise Routers Configuration
Guide - IPSec
.
l
If the settings of IKE proposals are the same, go to step 2.
NOTE
If preshared key authentication is used, configure a preshared key for each peer. The preshared keys of
peers that establish a connection must be the same. If not, run the
pre-shared-key
command to change the
preshared key.
Huawei AR2200-S Series Enterprise Routers
Troubleshooting
12 VPN
Issue 01 (2012-01-06)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
378