processing steps is as follows:
1.
Route lookup is done in the routing table and a list of all matching routes is assembled. The
routes in the list must cover the exact same IP address range (further explanation of this
requirement can be found below).
2.
If the route lookup finds only one matching route then that route is used and balancing
does not take place.
3.
If more than one matching route is found then RLB is used to choose which one to use. This
is done according to which algorithm is selected in the table's RLB Instance object:
•
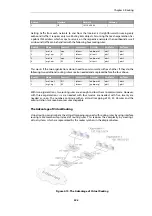
Round Robin
Successive routes are chosen from the matching routes in a "round robin" fashion
provided that the metric of the routes is the same. This results in route lookups being
spread evenly across matching routes with same metric. If the matching routes have
unequal metrics then routes with lower metrics are selected more often and in
proportion to the relative values of all metrics (this is explained further below).
Figure 4.5. The RLB Round Robin Algorithm
•
Destination
This is similar to Round Robin but provides "stickiness" so that unique destination IP
addresses always get the same route from a lookup. The importance of this is that it
means that a particular destination application can see all traffic coming from the same
source IP address.
•
Spillover
Spillover is not similar to the previous algorithms. With spillover, the first matching
route's interface is repeatedly used until the
Spillover Limits
of that route's interface are
continuously exceeded for the
Hold Timer
number of seconds.
Once this happens, the next matching route is then chosen. The
Spillover Limits
for an
interface are set in the RLB
Algorithm Settings
along with the
Hold Timer
number of
seconds (the default is 30 seconds) for the interface.
When the traffic passing through the original route's interface falls below the
Spillover
Limits
continuously for the
Hold Timer
number of seconds, route lookups will then revert
back to the original route and its associated interface.
Chapter 4: Routing
317
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...